
What Does SOC 2 Stand for?
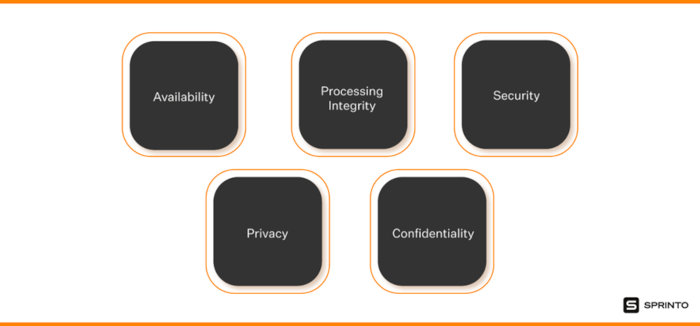
It stands for System and Organization Control 2 which is a reporting framework established by American Institute of Certified Public Accountants in 2010. Its purpose is to guide auditors in evaluating security protocol effectiveness of an organization. This report is for companies that handle customer data and store that data in the cloud. It covers security, privacy, confidentiality, processing integrity and availability. These trust service principles define the criteria used to manage customer data.
The purpose of SOC 2 is to help customers trust their service provider. Companies complying with this framework can be trusted and given projects where they receive customer data of their clients.
What Is SOC 2 Compliance?
It is a process to evaluate a service organization to see if it has in place all necessary processes, procedures and policies to maintain effective control over the data it handles. It complies with the TSC (trust services criteria) specified by AICPA.
TSC are a group of principles for evaluating controls related to security, privacy, confidentiality, processing integrity and availability of the system. These principles are used to evaluate the control an organization has over its processes. An organization looking to become SOC 2 compliant can choose which of the five TSC it wants to comply with.
The report can be prepared based on this specification. It is important to discuss this specification with the CPA firm before seeking the report.

What Is an SOC 2 Report?
This report shows a company’s compliance with the five criteria of SOC 2. The company can choose which of the five criteria it wants to include in its SOC 2 report. This selection can be based on the requirements relevant to its business practices.
Data provider can add extra controls for assessment. The auditor simply provides opinion on the controls and how they fit the service receiving company’s requirements. This is why it is necessary to hire an experienced auditor. Such a professional will have a better understanding of best practices and SOC controls that should be applied when preparing the report. The auditor provides an opinion that the company has excellent and effective controls in place and can be trusted for hosting data.
Any adverse or qualified opinion means the auditor has identified some issues with the internal controls. An SOC 2 report helps a service providing organization present its case of data protection boldly. It can show with this report why its customers should trust it. They are assured their data will be managed well and remain secure at all times.
SOC 1 vs. SOC 2
An SOC 1 audit is designed to provide auditor’s opinion on the internal controls of a service providing organization. These controls are related and limited to the financial statements of the customers. On the other hand, SOC 2 audit is related to security, privacy, confidentiality, processing integrity and availability of customer data.
SOC 1 covers controls related to securing and processing customer information in both IT and business processes. The SOC 2 report covers only the above specified five criteria. In this case, only the required principles of the five criteria can be included based on the regulatory requirements and nature of the operation.
SOC 2 vs. SOC 3
The main difference here is that the first report is restricted and not available publicly while the latter one can be published openly. Both reports are governed by AICPA standards. Even the auditor’s work remains same in both cases. The purpose of these reports is to comply with the TSC of AICPA. The way the report is presented is the key differentiator.
An SOC 2 report can be Type I or Type II but an SOC 3 report is always Type II. There is no Type I option with the SOC 3 report. SOC 2 reports are prepared only for restricted use and available to customers, customer’s auditor and service company. SOC 3 reports are published on the company’s website and made available to the general public. One reason for this is that SOC 3 report has fewer details and does not make available any patented, proprietary or sensitive data of the company.
SOC 2 Compliance Checklist
With the proliferation of cloud hosted applications, it has become necessary to become SOC 2 compliant. Preparing this report requires the auditor to follow some standard SOC checklist to ensure a successful compliance report. It is important to know that there is no official checklist from the AICPA.
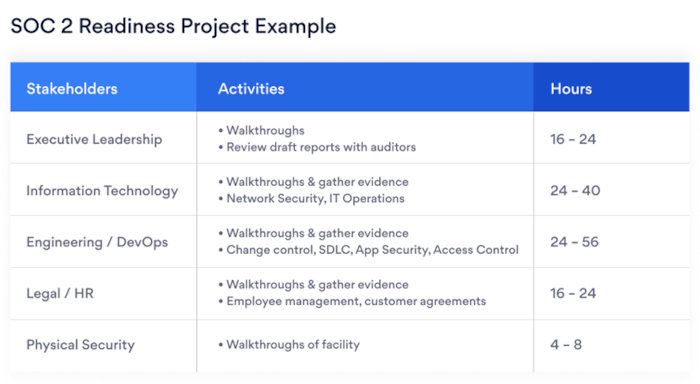
Some important points of the checklist include:
- Type of SOC 2 compliance report
- Scope of this audit
- Internal risk assessment
- Gap analysis and solutions
- Control at each step
- Readiness assessment
To prepare these reports, service providers must deal only with a third-party, independent and AICPA approved CPA.